Recognise and Remediate the Many Egos of Insider Threats
Over 90% of cyber security incidents are linked to people.
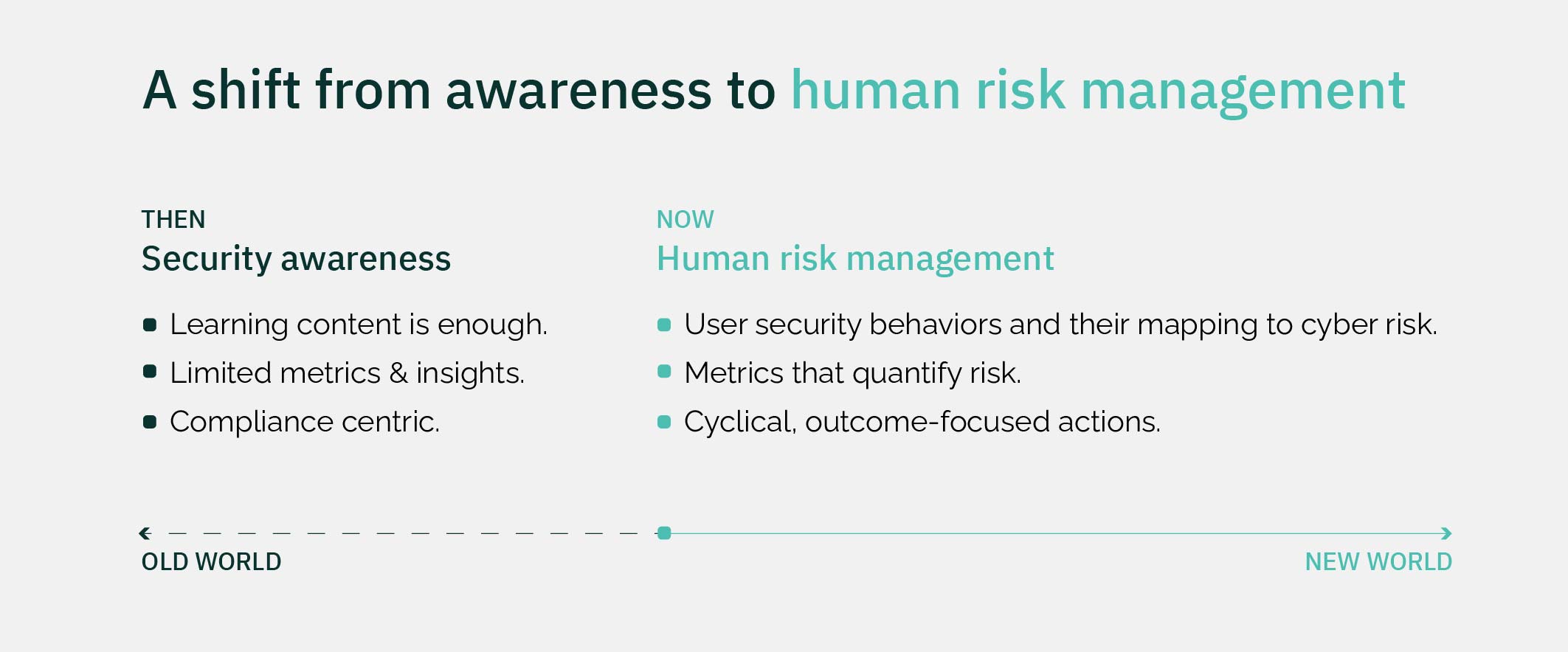
So why are organizations only paying lip service to human cyber risk? Why are tick-box training and phishing simulations still used? How can we make meaningful progress to quantify human cyber risk and change security behaviors?
An insider is defined as someone who exploits, or has the intention to exploit, their legitimate access to an organisation’s assets for unauthorised purposes. An insider could be a full time or part-time employee, a contractor or even a business partner. An insider could deliberately seek to join your organisation to conduct an insider act, or may be triggered to act at some point during their employment.
Employees may also inadvertently trigger security breaches through ignorance of rules, or deliberate non-compliance (due to pressure of work).
In a recent survey, “employees” topped the list of actors that companies are most concerned about exposing their organization to risk—both knowingly and unknowingly. Insider threats pose significant risks to businesses. Whether caused by carelessness or malicious intent, insider threats can be mitigated. To truly understand the risk of insider threats, one must first know the different forms that they can take.
They can be categorised as:
- disgruntled employees,
- corporate spies,
- accidental exposures,
- outgoing employees,
- fraudsters
each of which has unique motivations and behaviour patterns.
Policy development and understanding, effective awareness training and the right technical controls are paramount, particularly in highly regulated sectors processing and storing sensitive or highly confidential data. These need to:
- Reduce the risk of recruiting staff who are likely to present a security concern
- Minimise the likelihood of existing employees becoming a security concern
- Reduce the risk of insider activity, protect the organisation’s assets and, where necessary carry out investigations to resolve suspicions or provide evidence for disciplinary procedures
- Implement security measures in a way that is proportionate to the risk, such as monitoring

.png)
Download Cybsafe's Human Risk Management Guide here
To find out more about how we can resolve your IT issues please email or call us:
Send us an email Call us +44 (0)1462 416400













