Network security is a critical component of an organization's overall cybersecurity strategy, encompassing a range of technologies, processes, and practices designed to protect the integrity, confidentiality, and accessibility of computer networks and data. In today's interconnected digital landscape, where cyber threats are constantly evolving, robust network security is essential for safeguarding sensitive information and maintaining business continuity.

One fundamental aspect of network security is password management. Strong passwords serve as the first line of defense against unauthorized access. However, managing passwords across multiple systems and applications can be challenging for users, often leading to poor password practices. To address this, organizations are increasingly adopting password management solutions that generate, store, and automatically fill in complex, unique passwords for each account. These tools not only enhance security by encouraging the use of strong, diverse passwords but also improve user experience by reducing the cognitive burden of remembering multiple credentials. Advanced password management systems often integrate with multi-factor authentication (MFA) solutions, adding an extra layer of security by requiring additional verification beyond just a password.
Virtual Private Networks (VPNs) are another crucial element of network security, especially in the era of remote work and distributed teams. VPNs create encrypted tunnels between a user's device and the organization's network, ensuring that data transmitted over public networks remains confidential and protected from interception. This technology allows remote employees to securely access corporate resources as if they were directly connected to the internal network. Modern VPN solutions often include features like split tunneling, which allows selective routing of traffic through the VPN, and automatic connection based on network trust levels, enhancing both security and user experience.
As organizations move towards more flexible and cloud-centric architectures, Zero Trust Network Access (ZTNA) is emerging as a powerful approach to network security. ZTNA operates on the principle of "never trust, always verify," treating all network traffic, whether internal or external, as potentially hostile. This model replaces the traditional perimeter-based security approach with a more granular, identity-centric framework. ZTNA systems continuously authenticate and authorize users and devices before granting access to specific applications or resources, regardless of their location. This approach significantly reduces the attack surface and minimizes the potential impact of breaches by limiting lateral movement within the network.
Firewalls remain a cornerstone of network security, acting as a barrier between trusted internal networks and untrusted external networks, such as the Internet. Modern firewalls have evolved far beyond simple packet filtering, incorporating advanced features like stateful inspection, application-layer filtering, and intrusion prevention systems (IPS). Next-generation firewalls (NGFWs) go even further, offering deep packet inspection, threat intelligence integration, and even machine learning capabilities to detect and prevent sophisticated attacks. Cloud-based firewalls and firewall-as-a-service (FWaaS) solutions are gaining popularity, offering scalable protection for distributed networks and cloud environments.
Effective network security also involves continuous monitoring and analysis of network traffic to detect and respond to potential threats. Security Information and Event Management (SIEM) systems play a crucial role in this aspect, aggregating and analyzing log data from various network devices and security tools to identify patterns indicative of security incidents. Advanced SIEM solutions incorporate artificial intelligence and machine learning to enhance threat detection capabilities and reduce false positives.
Network segmentation is another important strategy in modern network security. By dividing the network into smaller, isolated segments or subnetworks, organizations can limit the spread of potential breaches and apply specific security policies to different parts of the network based on their sensitivity and requirements. Software-defined networking (SDN) and microsegmentation technologies are making this approach more flexible and granular, allowing for dynamic, policy-based network partitioning.
As networks become more complex and distributed, encompassing on-premises, cloud, and edge environments, the concept of Secure Access Service Edge (SASE) is gaining traction. SASE combines network security functions like ZTNA, FWaaS, and Secure Web Gateways (SWG) with WAN capabilities to support the dynamic secure access needs of digital organizations. This approach provides a unified, cloud-delivered security model that adapts to the location of users, devices, and applications.
In conclusion, effective network security requires a multi-layered approach that combines robust technologies, well-defined processes, and continuous vigilance. From fundamental practices like strong password management to advanced concepts like ZTNA and SASE, organizations must adopt a comprehensive strategy to protect their networks against evolving cyber threats. As the threat landscape continues to evolve, staying informed about emerging technologies and best practices in network security will be crucial for maintaining a strong security posture in an increasingly connected world.
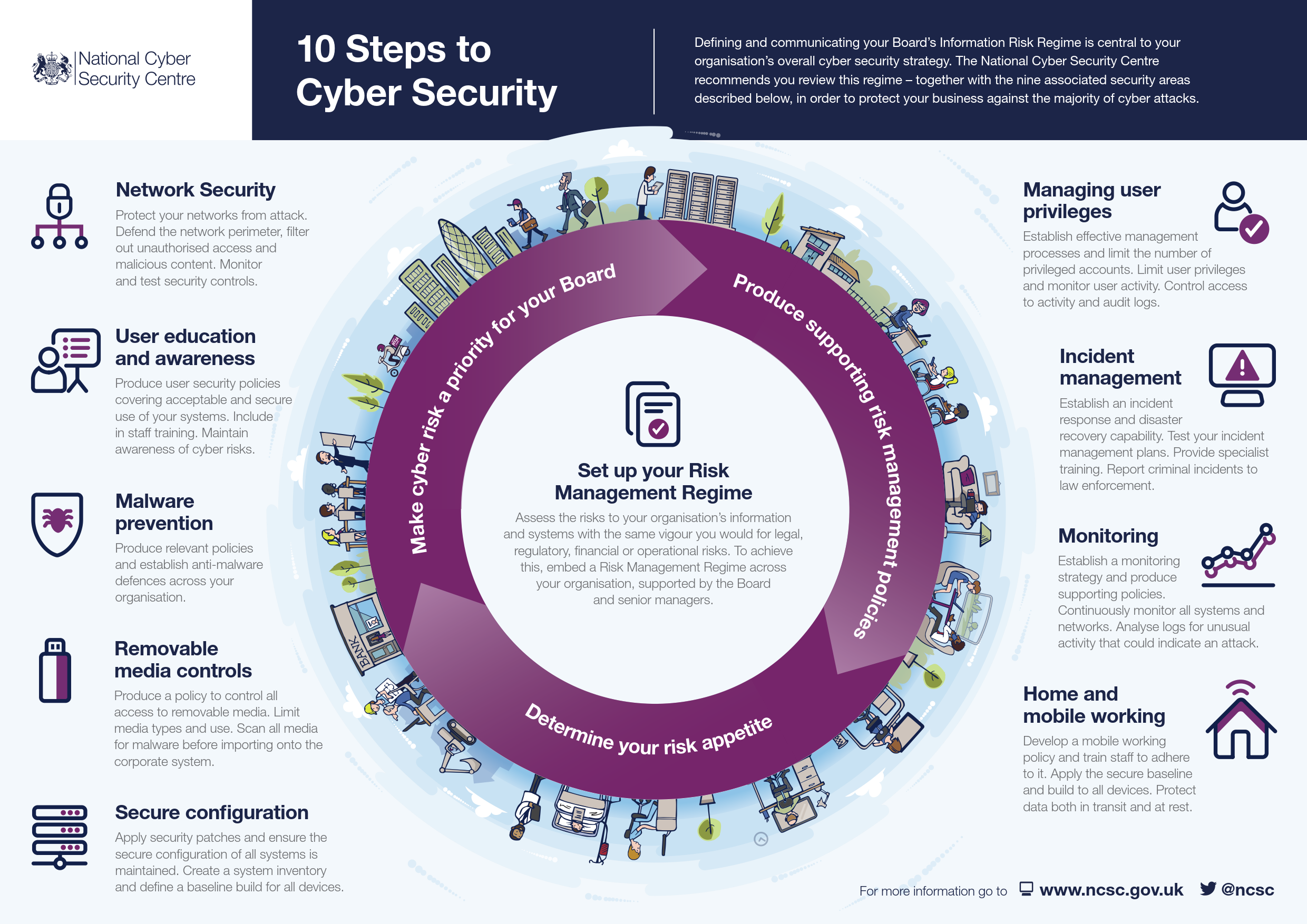
According to the NCSC (National Cyber Security Centre UK):
Networks need to be protected against both internal and external threats. Organisations that fail to protect their networks appropriately could be subject to a number of risks, including:
- Exploitation of systems: Ineffective network design may allow an attacker to compromise systems that perform critical functions, affecting the organisations ability to deliver essential services or resulting in severe loss of customer or user confidence.
- Compromise of information: A poor network architecture may allow an attacker to compromise sensitive information in a number of ways. They may be able to access systems hosting sensitive information directly or perhaps allow an attacker to intercept poorly protected information whilst in transit (such as between your end user devices and a cloud service).
- Import and export of malware: Failure to put in place appropriate security controls could lead to the import of malware and the potential to compromise business systems. Conversely users could deliberately or accidentally release malware or other malicious content externally with associated reputational damage.
- Denial of service: Internet-facing networks may be vulnerable to Denial Of Service (DOS) attacks, where access to services and resources are denied to legitimate users or customers.
- Damage or defacement of corporate resources: Attackers that have successfully compromised the network may be able to further damage internal and externally facing systems and information (such as defacing your organisation's websites, or posting onto your social media accounts), harming the organisation’s reputation and customer confidence.
The Cyber Security Breaches Survey is an Official Statistic, measuring how
UK organisations approach cyber security, and the impact of breaches.
Cyber security breaches and attacks remain a common threat.
Half of businesses (50%) and around a third of charities (32%) report having experienced some form of cyber security breach or attack in the last 12 months. This is much higher for medium businesses (70%), large businesses (74%) and high-income charities with £500,000 or more in annual income (66%).
By far the most common type of breach or attack is phishing (84% of businesses and 83% of charities). This is followed, to a much lesser extent, by others impersonating organisations in emails or online (35% of businesses and 37% of charities) and then viruses or other malware (17% of businesses and 14% of charities).
Among those identifying any breaches or attacks, we estimate the single most disruptive breach from the last 12 months cost each business, of any size, an average of approximately £1,205. For medium and large businesses, this was approximately £10,830. For charities, it was approximately £460
To find out more about how we can resolve your IT issues please email or call us:
Send us an email Call us +44 (0)1462 416400














