Information security risk management (ISRM) is a critical process for identifying, evaluating, and mitigating risks to an organization's information assets and systems.
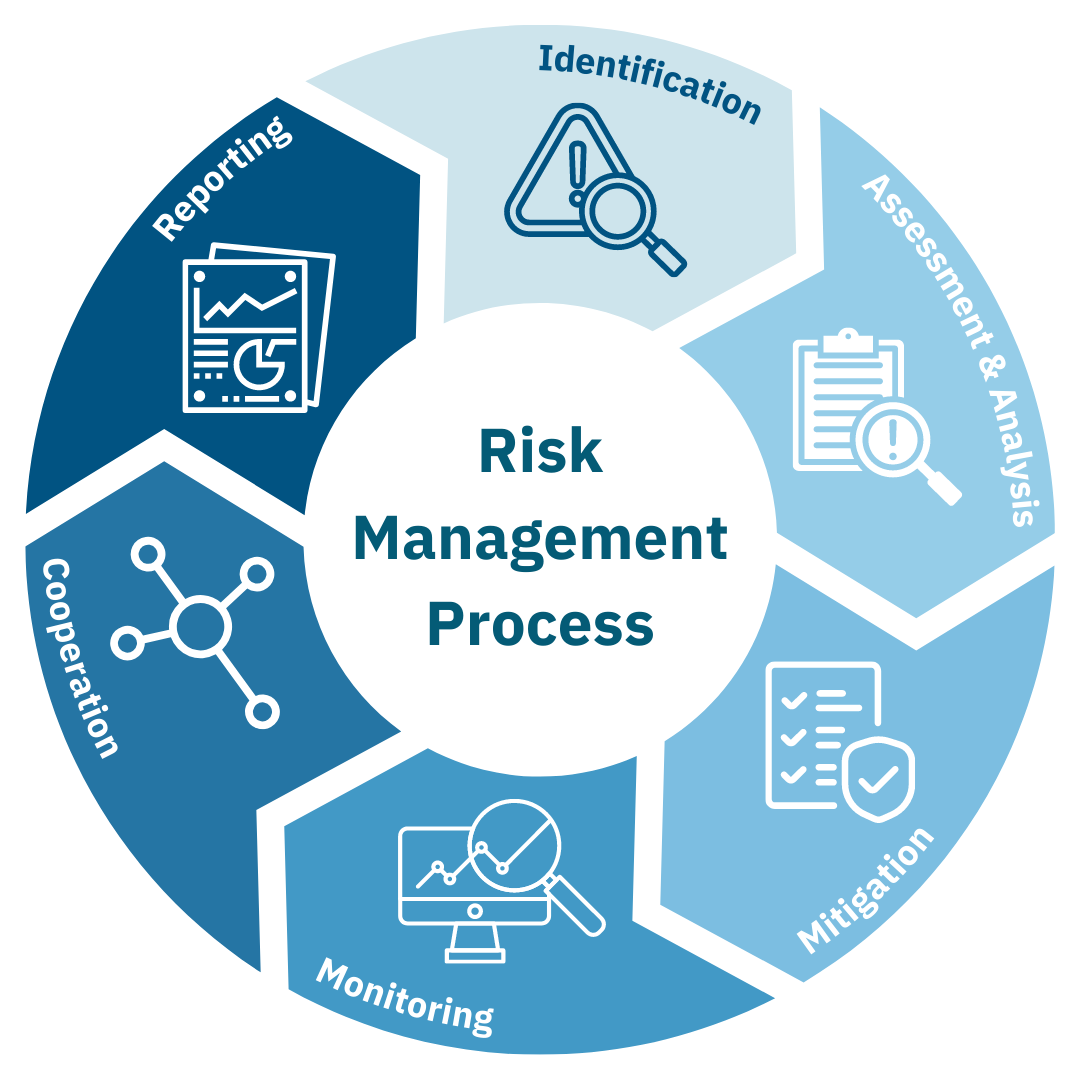
Here are the key steps involved in effective information security risk management:
Define Risk Assessment Methodology
The first step is to establish a clear methodology for assessing and managing risks. This includes:
- Defining risk criteria and how risks will be measured (e.g. impact and likelihood scales)
- Determining risk acceptance criteria
- Deciding on asset-based vs scenario-based approach
- Establishing roles and responsibilities
Identify Information Assets
Create a comprehensive inventory of all information assets, including:Hardware (servers, workstations, mobile devices, etc.),
- Software applications and systems
- Data (databases, files, backups)
- Network infrastructure
- Physical assets (facilities, equipment)
Identify Threats and Vulnerabilities
For each asset, identify potential threats and vulnerabilities:External threats (hackers, malware, natural disasters)
- Internal threats (employee errors, insider attacks)
- Technical vulnerabilities (software flaws, misconfigurations)
- Process/procedural vulnerabilities
Analyze and Evaluate Risks
Assess the likelihood and potential impact of each identified risk:
- Assign risk scores based on probability and impact.
- Prioritize risks based on their overall risk level
- Consider existing controls and their effectiveness
Develop Risk Treatment Plans
For prioritized risks, determine appropriate risk treatment options:
- Risk mitigation - implement controls to reduce risk
- Risk acceptance - accept risk within tolerance levels
- Risk avoidance - eliminate the risk source
- Risk transfer - share risk with third parties
Implement Controls
Put selected risk treatments into action:
- Deploy technical controls (firewalls, encryption, etc.)
- Implement administrative controls (policies, procedures)
- Provide security awareness training
- Establish incident response processes
Monitor and Review
Continually monitor the effectiveness of controls and reassess risks:
Conduct regular risk assessments (e.g. annually)
Perform vulnerability scans and penetration testing
Review incident reports and logs
Update risk register as new threats emerge
Report and Communicate
Keep stakeholders informed of the risk landscape:
- Provide risk reports to management and board
- Communicate changes in risk levels to relevant parties
- Document all risk management activities
By following these steps in a systematic and ongoing manner, organizations can effectively identify, assess, and manage information security risks. This process helps prioritize security efforts, allocate resources efficiently, and maintain an appropriate level of protection for critical information assets.
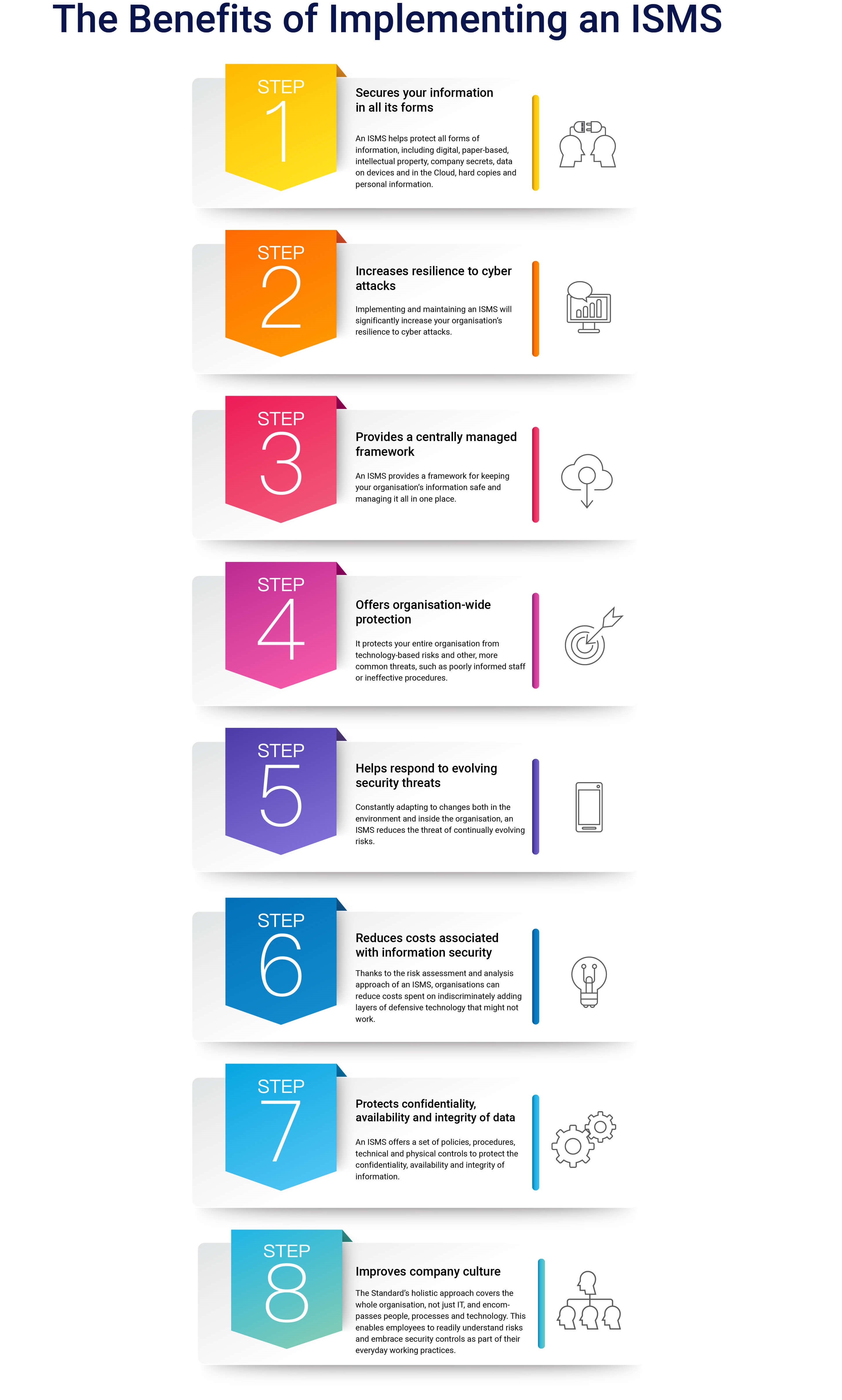
To find out more about how we can resolve your IT issues please email or call us:
Send us an email Call us +44 (0)1462 416400














